Whether you’re a developer, IT Manager or end-user, you’re familiar with the problems with passwords. They tax end-users, make your infrastructure vulnerable, and are susceptible to scalable attacks. Nok Nok Labs founded the FIDO Alliance in 2013 and brought its key inventions to create a framework of FIDO standards to help eliminate passwords.
With FIDO, end users get simple and unphishable authentication appropriate to their use case, developers get a single API that shields them from the complexity of authenticators and security mechanisms, and IT operators get a single backend that can select the right authenticator for a user by policy regardless of end-user platform or use case.
FIDO makes it possible to deliver strong authentication to users at population scale and changes the economics of authentication. FIDO protocols are now widely deployed commercially to over 3 billion users by the world’s largest Payments, Banking, Insurance, and Telecom companies. So far, FIDO protocols have addressed the mobile use case at scale across all operating systems and allowed authentication in browsers and on non-mobile devices through the use of the phone or a USB token as an authentication factor.
To reach an even wider audience, Nok Nok Labs has worked with Google, Microsoft and a few other partners to bring FIDO natively into Browsers and Operating systems. This new effort, best understood as “FIDO for Browsers”, sits next to the existing FIDO protocols that can be thought of as “FIDO for Mobile Apps”. The new work provides a standard API that allows users to log in with FIDO in a browser without a password and to use phones or tokens as authenticators.
FIDO2 is comprised of two parts. First, there is Web Authentication (aka WebAuthn), which is the JavaScript API (application programming interface), a W3C standard. The FIDO Alliance and the W3C worked together to develop this new standard that platform vendors are incorporating into major browsers, for example, Mozilla, Chrome, Edge, and WebKit. Second, there is the Client to Authenticator (CTAP) protocol. CTAP allows FIDO2-capable devices to interface to external authenticators over bluetooth, USB, or NFC. Web Applications do not use CTAP directly.
Here you see a high-level architectural view of FIDO2:
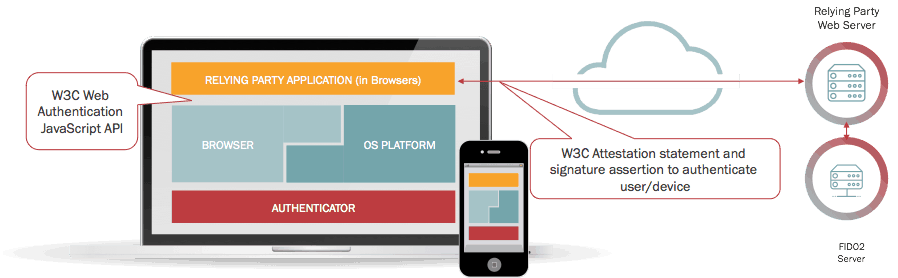
Here you see the 3 components on the client side:
- Web pages that use the W3C WebAuthn JavaScript API, for example, using an SDK from Nok Nok Labs
- The Web browser that implements the WebAuthn API and connects to the FIDO2 subsystem of the underlying operating system.
- Authenticators that the subsystem accesses to verify the user.
The server side has the relying party’s web application connected to a FIDO2 Server, for example, from Nok Nok Labs.
For more details on WebAuthn, you can review the W3C JavaScript API. As you may note, the WebAuthn API is extensive. Nok Nok provides an SDK with a simpler API that handles the lower-level REST (Representational State Transfer) and WebAuthn calls. With the Nok Nok SDK, integrating FIDO2 into your application is considerably simplified.
Platform support for FIDO2 and WebAuthn is evolving. It is supported on Edge, Chrome, and Firefox browsers, and in Android apps. WebAuthn is a W3C approved standard. Over time the list of platforms and browsers should expand, so stay tuned! You can also try out FIDO now.









